
How to Prevent Out-of-Bounds Document Sharing with Egnyte
Every day, your users access dozens of documents they need to do their jobs. However, many users fail to take basic steps to protect sensitive documents from leaving the organization. In sports, when a team loses the ball out of bounds, they have to go on defense. The same thing happens in business when you lose critical documents.
In this article, you’ll learn about the types of everyday documents that need protection but often don’t get it because users don’t realize the consequences. You’ll also discover steps you can take to find, monitor, and manage sensitive documents using Egnyte—you can even enable users to share them securely.
Is the Data Sensitive?
Your users already understand they have to be mindful about handling certain types of sensitive information. For example, salespeople know that customer credit card and financial information should be carefully guarded. Likewise, healthcare workers have been trained on HIPAA requirements to protect patient health information. However, many users are less cautious when handling “routine” office communications.
Here are some examples of information that is sensitive, but your users may not realize it:
- Employee contact list, org chart. A list of contact information for employees is very useful, and your users might email it to partners without concern. However, that information is valuable to recruiters wishing to poach talent from the organization, or scammers launching a phishing campaign.
- Commercial client lists and sales. If your company sells to consumers, your employees know that personally identifiable information (PII) should be protected for individuals. However, the same is true when you sell to companies rather than individuals. Companies need to maintain strict control over any information in public view, and that includes who they sell to or purchase from. Name dropping large customers or suppliers without permission can lead to serious consequences. Worse, improper exposure of large deals that materially affect financial accounting for either company could run afoul of SEC regulations for public companies.
- Business Plans. Information on upcoming products and features may be helpful when talking to customers, but competitors can use this information to gain advantage by preparing similar offerings, pricing, and marketing strategies. Worse, exposing pending partnerships prematurely can jeopardize the deals and cause them to fail.
How Can I Control Sensitive Data?
Egnyte provides a broad range of tools to not only protect sensitive data, but help your users interact with and share it securely. As a first step, the Egnyte Content Intelligence Engine scans all documents for sensitive information. This tool uses artificial intelligence to scan every word in every document in your repositories and uses context clues in the surrounding text to help it decide whether a string of digits is a part number or a Social Security number. It also includes a machine learning algorithm to get even more effective over time.
Egnyte has also pre-programmed dozens of data policies in categories that map to common regulations, such as privacy ( GDPR, CCPA), health (HIPAA, AMRA), and finance (GLBA, SOX, PCI-DSS). These policies will automatically detect and alert you to any sensitive information that would be subject to one of these policies.
You can activate any or all policies with a single click. Once you do, Egnyte will scan for sensitive data in the Egnyte repository, as well as any connected folders in Microsoft SharePoint, OneDrive, Google Drive, Box, Dropbox, and more. It will even complement a DLP system by monitoring the body and attachments in Exchange Online and Gmail. When sensitive data is discovered, you’ll be alerted on the Sensitive Content Dashboard, as shown below.
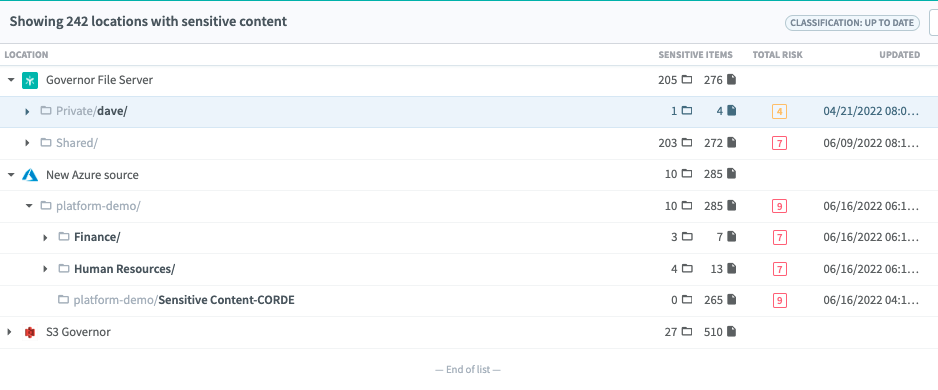
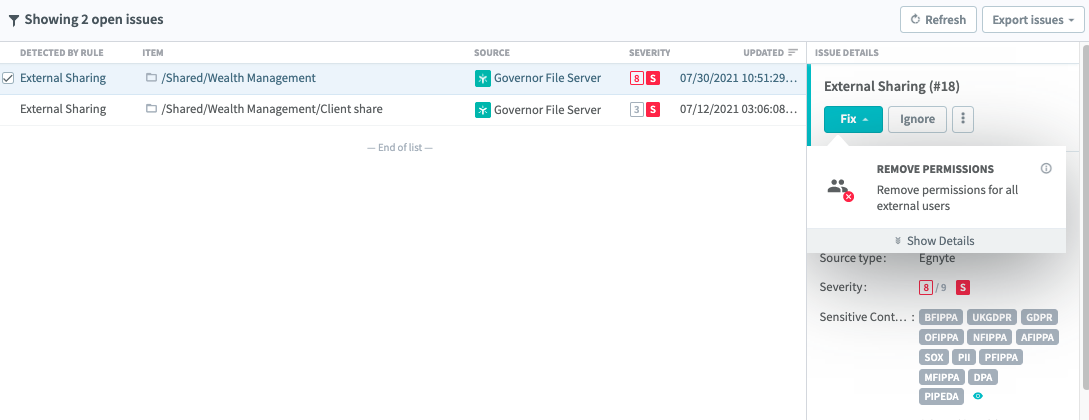
However, just locating sensitive information is not enough. You also need to protect it from your users sharing it out of bounds. For that, Egnyte monitors how your users share links to data and will alert you on the Issues Dashboard if sensitive information has been shared inappropriately.
In the screen below, two such issues have been detected, and Egnyte is recommending disabling external users with a single click without leaving the screen.
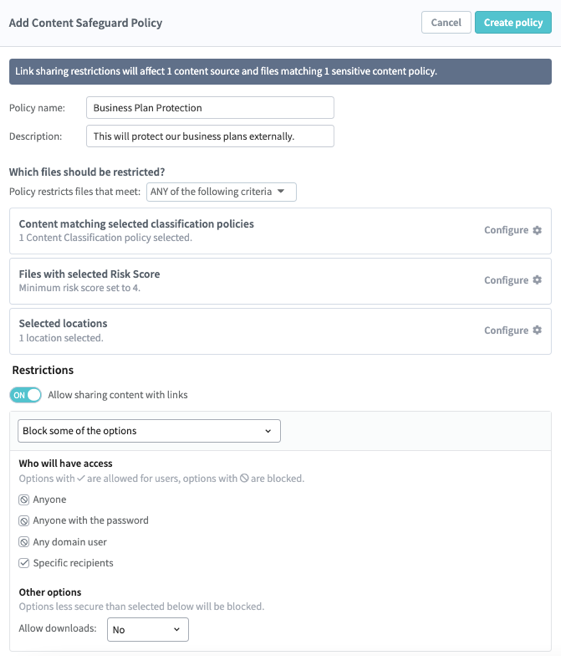
Finally, for more fine-tuned controls, Egnyte allows you to develop your own Content Safeguard policies. These policies can be based on a keyword list, user behavioral patterns, or document properties. For example, here is a policy to protect business plans.
How Can Users Still Share Information When They Need to?
Even with all the controls outlined above, your users will still need to share information as part of their jobs, and sometimes that information will be sensitive. Egnyte empowers your users with tools to make basic decisions themselves about how to protect sensitive information.
For example, when a user decides to share a file, they have many options to choose from, as seen from the following screen.
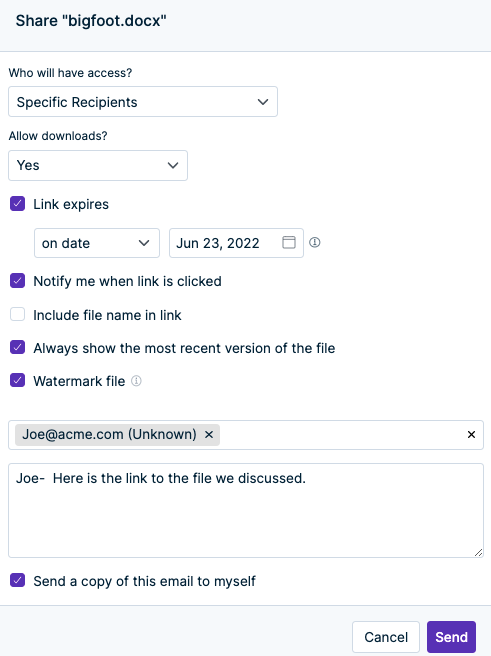
Users have the following options when they share files as links:
- Direct link for internal users. This is a quick, simple way to share files internally.
- Recipient control. The user can choose between sharing with anyone, sharing with anyone with a password, or sharing through a specific, verified recipient email address.
- Downloads. The user can decide whether the recipient can download a copy of the file, or simply view it in a preview in their browser. It’s also possible to require the user to download and install a small application to download and store the file locally as an encrypted file.
- Link expiry. The user can decide whether to allow the link to expire. If so, it can expire based on the number of clicks or a specific date.
- Notify sender. The user will receive an email when the recipient opens the link to the file.
- Most recent version. After a link is sent, the user can continue to modify the file. The recipient will always see the most recent version.
- Watermarks. This converts the file to a PDF to prevent modification and adds a watermark that shows the recipient information. This discourages downstream sharing.
- Copy link or direct email. Your user can copy a link and paste into an email, or simply launch the email from within the Egnyte application.
Manage Risk When Sharing Files
Sharing sensitive information out-of-bounds creates risk to your organization and your customers. However, you can manage this by:
- equipping your users to understand the risks of sharing inappropriately
- having a toolset that discovers, monitors, and blocks inappropriate sharing
- equipping your users to be responsible for managing risks themselves
Collectively, this provides a comprehensive approach to reducing risk while enabling users to do their jobs effectively. For more detailed information on how Egnyte helps manage out-of-bounds sharing, contact your Egnyte representative or follow the link below to take a self-guided tour of the platform.





