
Use Egnyte to Guard Against Insider Threats from Outgoing Employees
One of the biggest societal trends of 2021 has been the “Great Resignation.” For a variety of reasons—including a robust job market and the ongoing impact of the global pandemic—an average of 3.8 million U.S. workers quit their jobs on a monthly basis so far this year. That’s on pace to be the highest resignation rate on record, and the trend recently expanded to include international locations, such as Germany and Denmark.
Not only do resigning employees need to be replaced with new talent, employees who resign can also pose a significant insider threat risk to your organization.
The Great Resignation’s Impact on Insider Threats
Why do outgoing employees pose an insider threat risk to your company? Prior to resigning, employees and key contractors have access to their company’s sensitive data, including customer lists, product release plans, and financial records.
In certain industries, the labor market is so tight that most IT users continue to have access to sensitive data, even after they’ve notified their employers that they’re planning to resign. In the wrong hands, such sensitive data could easily be taken to a business competitor, shared with the media, or provided to users who don’t have legitimate access to the data in the first place.
The situation can be even riskier when employees have been notified of a potential layoff, but they still have access to data during an extended notice period. Similarly, when employees are not particularly good fits for job roles and/or are prone to making accidental errors, your company can face significant IT security risk.
All of these environments can be conducive to debilitating insider threats.
Why You Should Use Egnyte to Guard Against Insider Threats from Outgoing Employees
Companies spend an average of $644,852 on each insider incident, according to a 2020 report by the Ponemon Institute. The report also found that the average organization experienced three insider incidents in the past 12 months.
With Egnyte, you can analyze unusual user behavior related to sensitive data, particularly uncharacteristic file download volume by your users. Egnyte refers to such activity as “Unusual Access,” and in the steps outlined below you can see how easy it is to track and respond to these potential threats with the Egnyte platform.
How to Use Egnyte to Guard Against Insider Threats from Outgoing Employees
In order for your organization to minimize such threats, a recommended first step is to determine what files your users routinely access, and when they do so. Remember that an effective insider threat detection program should combine the data security best practices presented below with network security protocols and user education.
Set Issue Detection Thresholds
The first step to insider threat detection is to establish criteria that indicate potential unusual user access to sensitive data. With Egnyte, you can determine the following:
- Volume of files that your users have accessed, downloaded, and/or deleted
- Sensitivity of files that have been accessed
- Location of data access
- Time of day of data access
From the Egnyte platform dashboard, simply click on the menu icon, choose Settings, click on Analysis Rules in the left panel and then select Unusual Access. You will be presented with the menu below, where you can customize your settings.
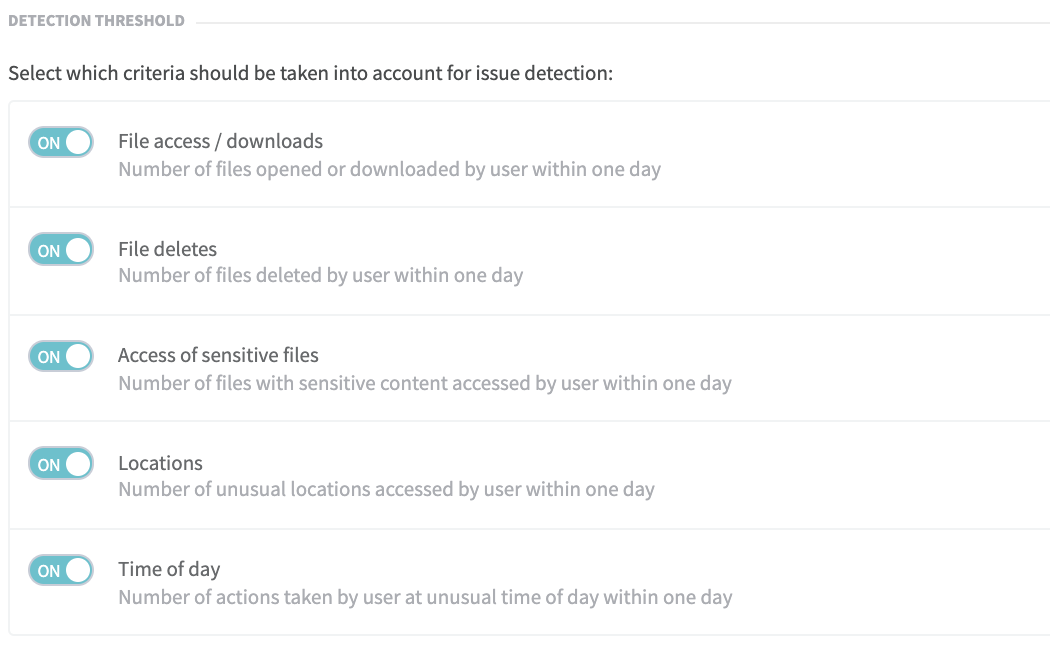
Set Unusual User Activity Benchmarks
On the Detection Threshold page, you can review the total number of Unusual Access issues that have been detected and set severity levels for issues that affect your environment. You can also establish thresholds that control how far users’ activity needs to deviate from normal usage patterns before an anomaly is detected.
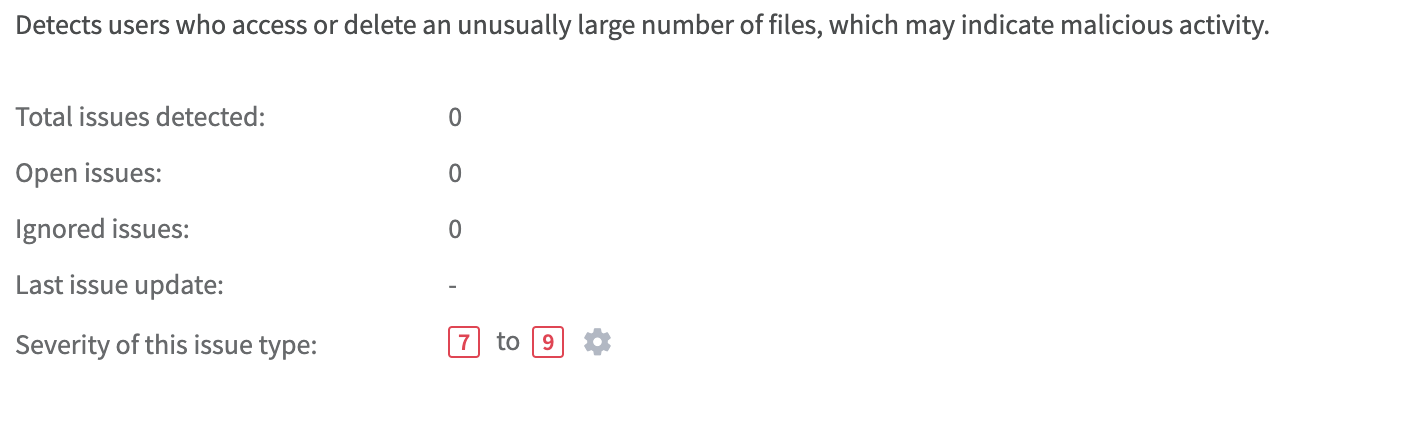
Set Parameters That Trigger Issues
You can also establish a minimum number of files that need to be accessed by a particular user in order to trigger an issue.
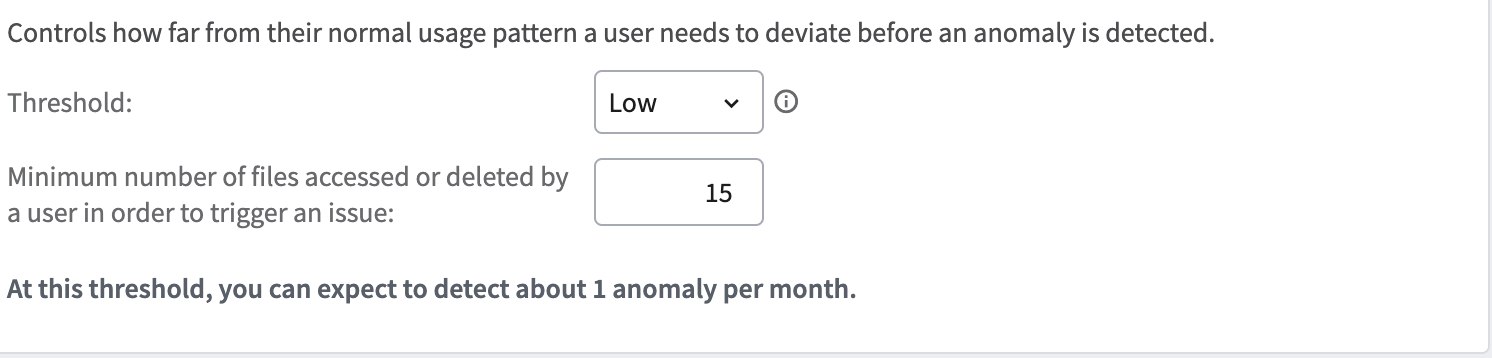
In the example above, a user who accesses or deletes 15 files during the assessment period will trigger an issue.
Review Anomalous File Access by Specific Users
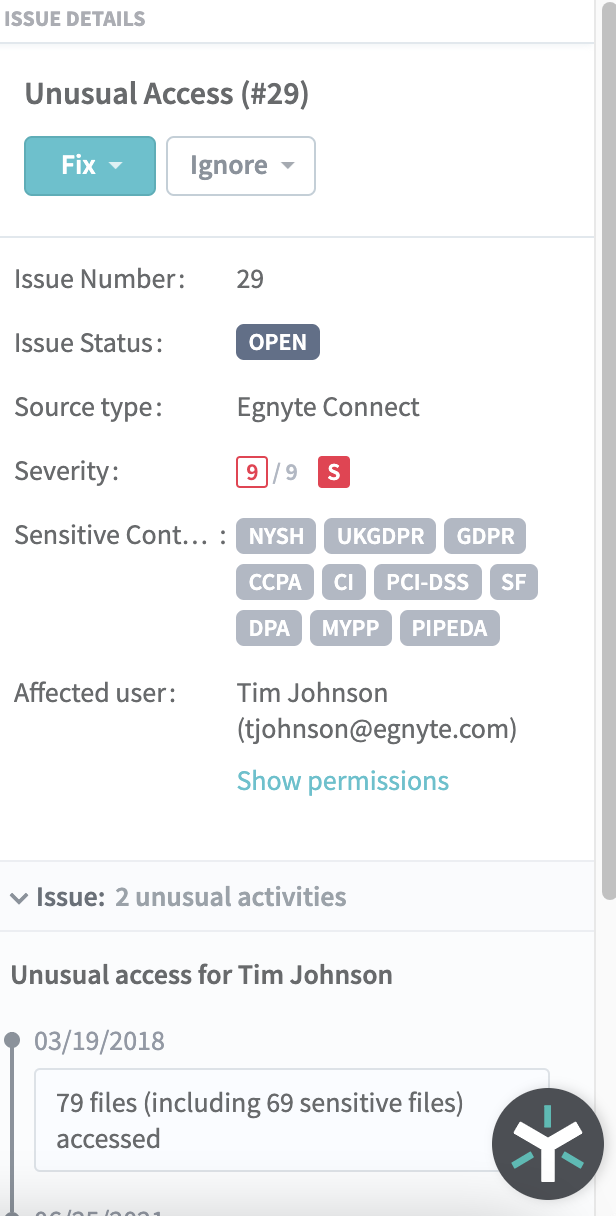
After you’ve set issue detection parameters, you can easily review anomalous behavior for particular users, as seen in the example below.
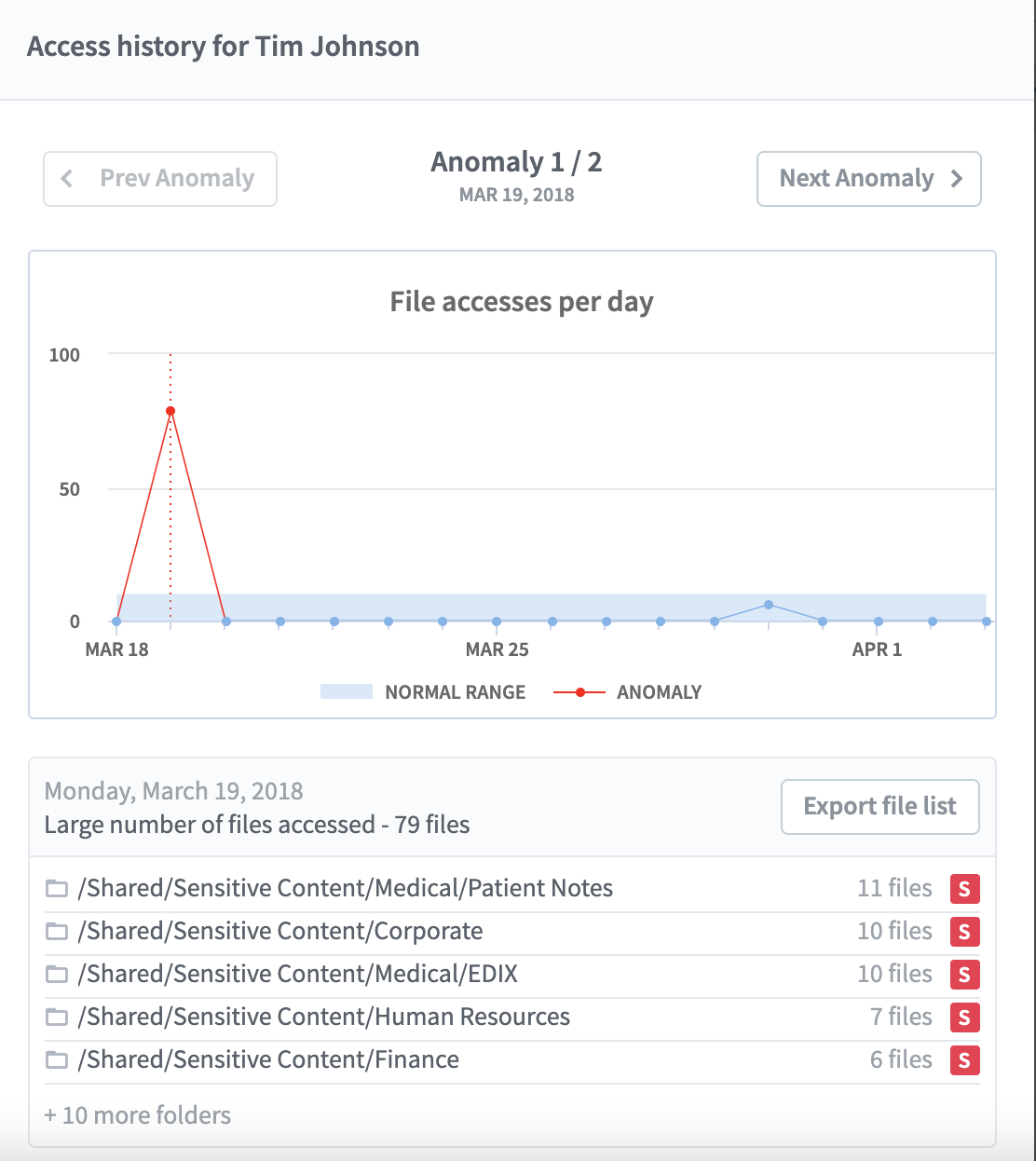
In the classic example above, you can see that user “Tim Johnson” accessed a total of 79 files on a single calendar date, which is substantially higher than the number of files he accessed on other business days. The accompanying recap indicates that Tim accessed a large number of files that contain sensitive information during the time period, including 21 files containing medical data, 10 files containing corporate data, seven files containing human resources data and 6 files containing financial data.
Based on the volume of sensitive data that Tim accessed—across a wide range of content types—the situation would merit further review by your IT team.
Assess Which Industry and Data Privacy Regulations Apply
In the Issue Detail view, you can see that Tim accessed a vast amount of sensitive data that’s subject to GDPR, UK GDPR, CCPA and PCI-DSS regulations, so that’s one more reason why you should investigate further.
And that's it. In those quick, easy-to-follow steps, you learned how to detect and review Unusual Access with Egnyte, so you can investigate and prioritize such situations.
Finally, it’s important to remember that unusual activity doesn’t automatically mean malicious or careless activity. For example, you could investigate Unusual Access activity and find that a particular set of company users were working on a special project that involved lots of sensitive content, so all of their access was completely legitimate and above board.
Click on the Data Governance Test Drive link below to try Egnyte’s capabilities for yourself.





