
Mastering Compliance in M365 Cloud Office Environments
With the explosive growth of Microsoft 365, many companies are suddenly experiencing content sprawl at an unprecedented rate. What is content sprawl? It's when your employees create unstructured content (files, chats, video) in the course of their workday, which then gets stored in multiple repositories, like SharePoint and OneDrive. Accelerate that in the context of a remote workforce, and you suddenly have content sprawling all over the place.
The rapid adoption of Microsoft Teams (which grew 800 percent in 2020) is fueling a compliance crisis, as content becomes more far-flung and compromises the requisite visibility for meeting regulatory standards. Fortunately, there are a few things that IT leaders can do to get ahead of compliance gaps in M365 before the headaches, and the regulators, come calling.
1. Get a Realistic Portrait of Your M365 Architecture
Understanding the compliance gaps and vulnerabilities inside M365 Office environments is a key first step to improving your overall compliance posture. Many organizations elect to configure M365 services like SharePoint, Teams, and OneDrive in a way that enables anyone to create Teams, Team Sites, and Channels. When multiplied across many users, the resulting file sprawl becomes unmanageable for IT administrators and compliance teams. For example, each time a user creates a new Microsoft Team, they are, in fact, provisioning many services:
- A new Microsoft Teams team
- A new SharePoint Online team site
- A new Outlook group and calendar
- A new Power BI workspace
- A new Planner plan
This underscores why it is so difficult for many companies to accurately map their M365 architectures -- it is constantly shifting and growing. These ad-hoc groups create complex, overlapping circles of access to files. Companies must understand how these seemingly benign tools contribute to data sprawl and inconsistent permissions and access issues that make cyber auditing, breach reporting, and DSARs more difficult. For OneDrive For Business there are 78 settings spread across 18 different locations that manage how data is protected, stored, and shared (up from 65 last year). The potential for misconfigurations complexity are very common reasons for a breach, as presumably also a compliance problem.
2. Inventory Regulated Data
There are hundreds of data privacy laws on the books and many more under consideration in statehouses and global legislative bodies. Each has a range of different requirements for auditing, data subject access requests, consumer disclosures, data handling and breach reporting. Though provisions vary, each requires a mechanism to locate and identify affected data before more sophisticated protocols can be put in place.
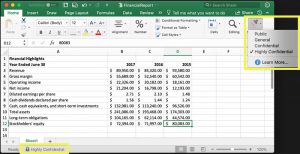
Manual Sensitivity Labeling in M365 This is especially important because data regulations constantly evolve, sometimes before they’re even enacted. When the California Consumer Protection Act (CCPA) was initially passed, the scope far exceeded what became the final version of the law as it is known today. In the interim months, companies that were preparing for CCPA implementation began a laborious process of finding and tagging files that contain CCPA data. When only a few months later, the law was changed to capture a narrower scope of PII, many discovered they’d need to repeat the process or end up with thousands, or millions of false positives.M365, and SharePoint in particular, still rely on end-user tagging as the primary means of labeling and protecting files that contain regulated data like driver’s license numbers, or patient IDs. Out-of-the-box generic labels like “public” or “confidential” leave much room for interpretation and are difficult to update in response to changes in regulatory requirements.
3. Rein in End-User Tagging
M365 does offer varying degrees of automated tagging capability, depending on the license type and where data resides in (e.g. OneDrive vs. Docusign). Businesses that can support the administrative demands of Microsoft Information Protection can take advantage of this, while many others opt for manual tagging capabilities baked into most M365 packages. Without specific guidance and training, there tends to be poor adherence to any formal information architecture (data classification, tagging, labeling, navigation). Tag fatigue happens, and when it does, end-users typically opt for the fastest or most convenient option. But this can have real consequences. Marking something “public” that contains a consumer’s personal data can expose businesses to fines under sweeping privacy laws like CCPA and GDPR, not to mention erode customer trust. Automating data classification and tagging is the best way to avoid the pitfalls of manual labeling. This can be done natively in M365 at the highest licensing tiers, but companies may also opt for third-party classification and governance solutions that connect to Microsoft cloud apps like SharePoint and OneDrive and on-premises Windows File Servers. Ultimately, those who settle for manual tagging in M365 may find themselves pursuing an upgrade anyway. While manual sensitive data labeling is enabled at some lower license levels, the ability to conduct false positive reviews to validate the accuracy of those labels is not. If ensuring that labels are applied correctly is a priority, Microsoft customers will need to pay for it, or build their own complex (potentially error-prone) manual tagging systems.
4. Decode Your M365 License Agreement
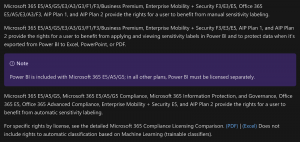
Microsoft Information Protection Licensing Breakdown: Automatic Sensitivity Labeling vs. Manual The sheer breadth of Microsoft’s available governance, security, and compliance modules and licensing options can make it difficult to track and understand exactly which functionality is available under a given license. Microsoft customers must carefully evaluate which features are most important for their specific compliance needs, and whether their plan supports it. With more than 60 features and functions across 20+ licensing tiers, this can be daunting, but it’s worth reading the fine print. For example, as of October 2020, an M365 E3 license includes access to the new Compliance Manager dashboard, but a quick look under the hood reveals that most of the strongest functionality is not usable without an upgrade to the E5 license. Those include automated classification and keyword-specific retention policies -- both extremely valuable for compliance with GDPR, CCPA, and financial regulations. For important features like sensitive data labeling, interrogating the license terms can help determine what exactly is included, and whether it covers the apps that users really need (e.g. PowerBI).
5. Augment Compliance Coverage for Third-Party Sources
M365’s compliance tools can be valuable for files created in the Microsoft Office suite or housed in M365 apps like SharePoint or Exchange, but what about the world of data beyond M365? Nearly half of CIOs say that the needs of different departments require that data reside in multiple repositories, many of which are not Microsoft-owned. These include CMS systems (e.g. SalesForce), legacy CIFS repositories, cloud storage (e.g. Google Cloud, AWS), productivity apps (e.g. Box, Google Workspace) and email systems (e.g. G Suite). As of October 2020, automated sensitivity labeling for non-Microsoft sources was only available at the highest license levels. Even manual sensitivity labeling requires the addition of the Microsoft Cloud App Security tool. These limitations could force a costly upgrade for companies wishing to extend sensitivity labeling beyond SharePoint and OneDrive. For smaller IT teams, the administrative lift of managing yet another security service for third-party data discovery may be prohibitive. Even at the top end, some elements of third-party coverage are lacking. For example, M365 doesn’t currently support data subject access request queries across non-MS repositories without first importing the data into Office 365. Even companies that go “all in” on Microsoft compliance may require another tool to execute DSARs in accordance with GDPR and CCPA for common third-party applications. To learn more about Egnyte’s approach to managing compliance in M365 and beyond, visit: https://www.egnyte.com/solutions/regulatory-compliance.
Photo by Philipp Katzenberger on Unsplash.






