Cybersecurity Maturity Model Certification (CMMC) Compliance
Updated in October 2024 to Reflect the CMMC Final Rule
The U.S. Department of Defense (DoD) released the first version of the Cybersecurity Maturity Model Certification (CMMC) in 2020 and updated it to CMMC 2.0 in November 2021. CMMC 2.0 was further updated with a Final Rule from the DoD in October 2024.
CMMC is part of an ongoing effort to secure the DoD’s supply chain and The Defense Industrial Base (DIB). Historically, cybersecurity standards have been built into acquisition programs to assure that contractors and subcontractors meet DOD’s cybersecurity requirements. CMMC was created to protect DIB contractors (the worldwide industrial complex that enables research and development, as well as design, production, delivery, and maintenance of military weapons systems, subsystems, and components or parts, to meet the U.S. military’s requirements) from potential cybersecurity threats.

CMMC is based on the National Institute of Standards and Technology Special Publication (NIST SP) 800-171 Rev. 2 and NIST SP 800-172
What is CMMC Compliance?
CMMC 2.0 Levels
CMMC measures cybersecurity maturity, or capability and progression within an organization's security program, through three levels. Each level has detailed processes and requirements that are necessary for CMMC compliance.
To meet CMMC compliance requirements at one of the three levels, contractors must demonstrate achievement in the desired level as well as the lower levels. In addition, contractors “must demonstrate both the requisite institutionalization of process and the implementation of practice” (as detailed in the diagram below).
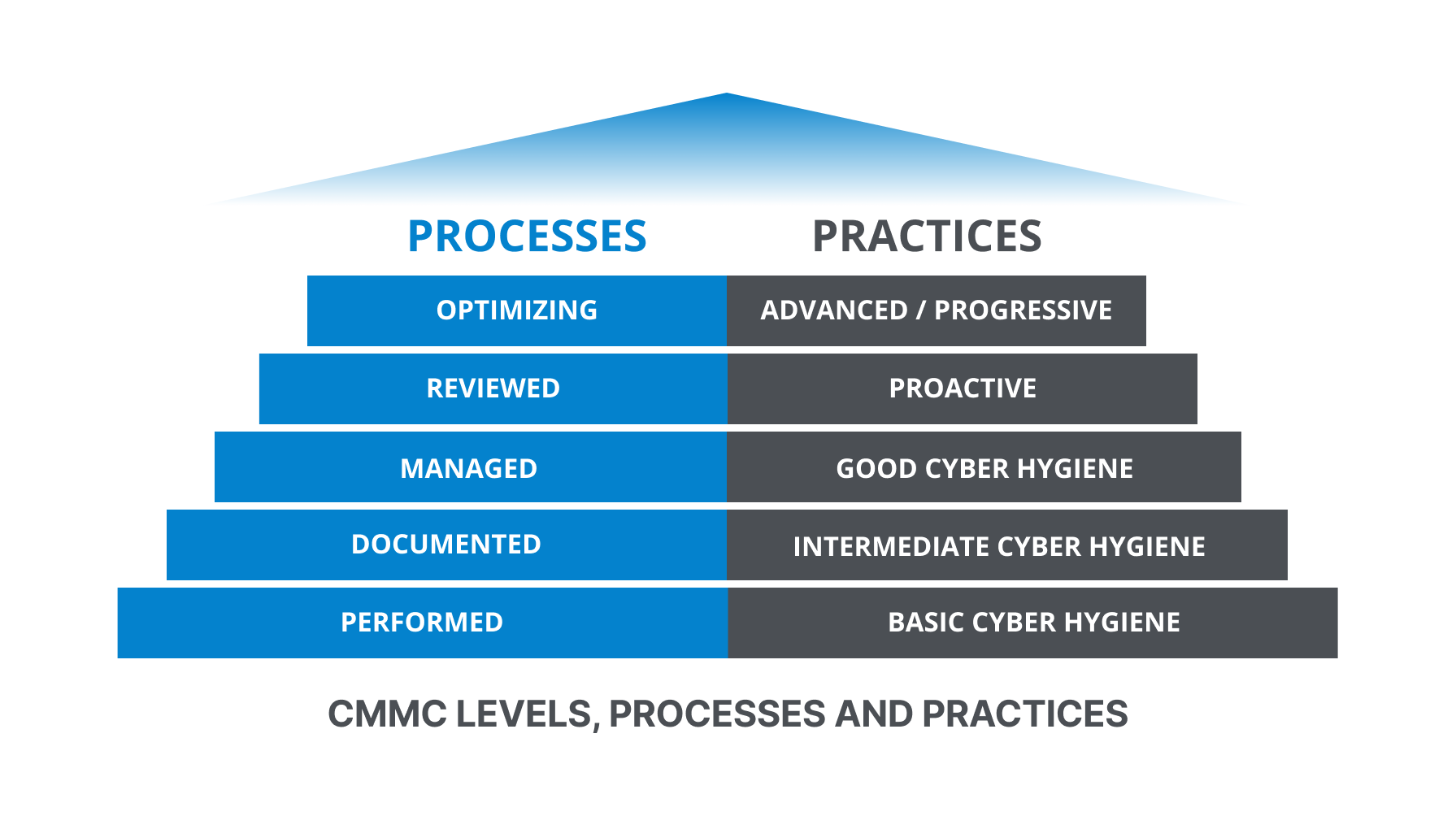
Because not all contractors or subcontractors manage the same sensitivity of defense-related data, CMMC compliance requirements are presented in levels. When CMMC 2.0 is fully implemented, DoD requests for information (RFI) and requests for proposal (RFP) will include which CMMC compliance level is required for a given contract. Before consideration, a contractor will be assessed by a third-party assessment firm and given a score based on its assessment.
CMMC 2.0 Levels
CMMC compliance levels take into account the sensitivity of government data that contractors work with and require them to adhere to CMMC levels that are assigned to particular projects. The CMMC 2.0 compliance levels range from Level 1 to Level 3. We provide specifics for each of the three levels later in this overview.
| What Is Controlled Unclassified Information (CUI)? CUI is information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls. |
CMMC compliance levels align with contractors’ cybersecurity practices and the sensitivity of DoD data they manage, as well as the types and consequences of potential threats.
The three CMMC compliance levels have the following high-level goals:
- Level 1: Safeguard Federal Contract Information (FCI)
- Level 2: Protect CUI
- Level 3: Protect CUI and reduce the risk of advanced persistent threats (APT)
Additional details about the various CMMC 2.0 levels appear below.
Level 1
Level 1 applies to DoD contractors and subcontractors who manage FCI only. When CMMC goes into full effect, Level 1 organizations will be required to perform annual self-assessments and have their results submitted into the Supplier Performance Risk System (SPRS).
Level 2
Level 2 applies to DoD contractors and subcontractors who manage CUI. A small proportion of Level 2 organizations (approximately 5%) will be required to perform annual self-assessments and submit their results into SPRS, as outlined in the Level 1 description above.
The remaining 95% will be subject to formal triennial assessments by a Certified Third-Party Assessor Organization (C3PAO). Their results will be submitted into the Enterprise Mission Assurance Support Service (eMASS).
Level 3
Level 3 mainly applies to the largest DoD contractors, who manage the DoD’s most sensitive contracts. In addition to being subject to CMMC Level 2 requirements, Level 3 organizations are subject to 24 NIST SP 800-172 requirements that are assessed by the Defense Contract Management Agency Defense Industrial Base Cybersecurity Assessment Center (DCMA DIBCAC). Similar to Level 2, Level 3 companies’ results need to be submitted into eMASS.
Who Must Comply with CMMC?
All DoD contractors or subcontractors must be CMMC compliant by early 2025.
The first step is to determine whether CMMC applies to your organization. CMMC requirements apply to your organization if you’re a DoD contractor (and/or subcontractor) who manages (processes, stores, or transmits) Controlled Unclassified Information (CUI) or Federal Contract Information (FCI).
Level 2 organizations are generally subject to triennial third-party assessments by a Certified Third-Party Assessor Organization (C3PAO). Level 3 organizations are subject to triennial Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) assessments.
Since CMMC compliance requirements apply to all contractors who engage directly with the DoD and their subcontractors, it has a significant impact on thousands upon thousands of organizations. These include contractors in areas such as:
- Critical infrastructure
- Defense
- International defense
- Law enforcement
- Military Intelligence
- Legal
- Natural resources
- Procurement and acquisition
The reach of CMMC is expansive. A DIB organization with FCI, even if it does not manage or produce CUI, must meet the requirements for CMMC compliance at Level 1.
DoD gave contractors several years to meet the requirements set forth in the three levels for CMMC compliance. Since 2020, thousands of vendors have worked to understand just what is required of their businesses to become CMMC compliant. Contractors that have not met the CMMC compliance requirements by 2025 risk losing the ability to bid on and ultimately win valuable DoD contracts.
What is Required of Businesses?
CMMC compliance requirements are based on the certification level being sought. Each level builds on the previous one, meaning that Level 3 must achieve the most stringent requirements, as well as all of those set forth in the first two levels.
The level of certification required for a contractor to meet CMMC compliance requirements will be specified in the DoD’s RFIs and RFPs. The higher a contractor’s CMMC level, the more DOD contracts that are potentially available.
DoD subcontractors are subject to the same CMMC compliance level as prime contractors. The level of CMMC compliance is dictated by the level specified in the contract and the information that is shared with subcontractors. For instance, a subcontract may only have to meet CMMC compliance requirements for a lower level if the subcontractor’s work is registered as less sensitive.
It should also be noted that if a DoD contractor or subcontractor works with a Managed Services Provider (MSP) or Managed Security Service(s) Provider (MSSP), the MSP or MSSP must be at the same CMMC compliance level as the contractor or subcontractor.
The 14 CMMC compliance capability domains are as follows:
1. Access Control (AC)
2. Audit and Accountability (AU)
3. Awareness and Training (AT)
4. Configuration Management (CM)
5. Identification and Authentication (IA)
6. Incident Response (IR)
7. Maintenance (MA)
8. Media Protection (MP)
9. Personnel Security (PS)
10. Physical Protection (PE)
11. Risk Management (RM)
12. Security Assessment (CA)
13. System Communications Protection (SC)
14. Systems Information Integrity (SI)
Understanding CMMC Requirements
CMMC’s requirements include:
- Level 1: 15 total practices
- Level 2: 110 requirements aligned with NIST SP 800-171 Rev. 2
- Level 3: 134 requirements, 110 of which are based on NIST SP 800-171 Rev. 2, with the remaining 24 requirements based on NIST SP 800-172
CMMC Level 1 Requirements
At base, CMMC compliance requires foundational cyber hygiene and that security processes are performed—and annual self-assessments are required. Most of those standards are currently met by federal contractors.
There are 15 requirements for CMMC compliance at Level 1, as detailed in FAR clause 52.204-21: Basic Safeguarding of Covered Contractor Information Systems.
CMMC Level 2 Requirements
To achieve CMMC compliance at the second level, the requirements of Level 1 must be met, along with additional security requirements that are included in NIST SP 800-171—Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations (Rev. 2).
CMMC Level 3 Requirements
To achieve CMMC compliance at the third level, the requirements of Level 1 and 2 must be met, along with 24 more security requirements that are included in NIST SP 800-172— Enhanced Security Requirements for Protecting Controlled Unclassified Information (Rev. 2).
CMMC’s Implications
For DoD contracts:
- CMMC compliance is a “Go/No-Go” DoD proposal evaluation criterion.
- CMMC Level 2 will likely be required for most DoD contracts.
- Compliance with NIST regulations for a baseline level of cybersecurity is only a minimum requirement for consideration of a bid, and additional factors will come into play when the DoD makes its final contracting decisions.
- Prime contractors are contractually responsible for the supply chain’s cybersecurity hygiene, but DoD subcontractors are also required to be CMMC compliant.
- MSPs and MSSPs are subject to CMMC 2.0 certification at the level of the contractor or subcontractor they’re working with, for their CUI-scoped processing environments.
- You should reach out to the DoD directly, if you have questions about your company’s current or future contracts with the agency.
Preparing for a CMMC Assessment
For many DoD contractors and subcontractors, the ultimate goal of the CMMC compliance process is to successfully complete a CMMC assessment, so that the organization can continue to contract with the DoD.
Here are best practices to jump-start that process:
Determine Required Certification Level for CMMC Compliance
CMMC Level 1 is for DoD contractors that do not manage CUI.
Level 2 is focused on DoD contractors that manage CUI.
Level 3 is the highest level of CMMC compliance and applies to DoD contractors that need to protect CUI targeted by sophisticated cyber-adversaries (e.g., international crime syndicates, malicious nation-states) or advanced persistent threats (APTs).
Assess Your CUI Environment
Determine which assets and systems are in scope, including all assets that directly or indirectly come into contact with Controlled Unclassified Information (CUI).
Complete a Readiness Assessment
Determine which aspects of the cybersecurity program are already in compliance with CMMC’s requirements, and which ones require additional focus, including people, systems, processes, and technology. Extra attention should be paid to how CUI is stored, processed, and transmitted. It is also important to have a clear understanding of who in the organization is responsible for establishing and maintaining CMMC’s controls.
Identify Remediation Steps
Assess risk associated with security gaps and quantify the steps needed to achieve compliance at the appropriate level.
Create a Compliance Roadmap
Develop a plan to remediate security gaps based on priorities and resources.
Implement and Maintain Ongoing Monitoring Activity
DoD requires contractors to monitor systems on an ongoing basis and report cyber-incidents.
Win-Win with CMMC Compliance
CMMC compliance is required for all contractors or subcontractors that work with the DoD. The tiered approach to CMMC compliance makes it achievable for most contractors, especially with the changes to CMMC that enable more organizations to perform self-assessments, rather than having to undergo formalized assessments by C3PAOs.
CMMC 2.0 aims to increase accountability for companies to implement and maintain effective cybersecurity programs, while reducing barriers to compliance with DoD requirements. Aligning the model with NIST also helps streamline compliance for organizations, since the technical requirements are similar.
Regardless of what it takes to achieve CMMC compliance, the effort will provide significant benefits to your organization, from a cybersecurity standpoint. And, organizations can be confident that many current cybersecurity risks are addressed by adherence to CMMC 2.0’s standards, since CMMC 2.0 is aligned with NIST guidelines that are regularly updated to address today’s evolving cyberthreat landscape.
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 22,000+ customers with millions of users worldwide.
Last Updated: 30th October, 2024