Group Policy
Group policy is a Microsoft Windows management feature that makes it possible to control multiple users’ and computers’ configurations. Primarily intended for enterprise use, Group Policy can also be used by individuals who manage smaller configurations (e.g., in a home). On its own, a setup in Group Policy only applies to a single computer, but it is combined with Active Directory for enterprise use.

User and computer configurations can be managed through Group Policy Settings and Group Policy Preferences. Collectively referred to as Group Policy Objects, these policies are based on a collection of individual Group Policy settings. Group Policy Objects can be applied locally to a Windows computer through the operating system or through Active Directory.
Many organizations use a combination of local and Active Directory Group Policy objects. The local policy settings provide security when the user is not logged into a domain, while Active Directory Group Policy objects apply once the user has logged in.
Group Policy Settings and Group Policy Preferences can be managed in an Active Directory Domain Services environment through the Group Policy Management Center or GPMC. To administer Group Policy settings from a desktop, Group Policy management tools are used.
Let’s jump in and learn:
What Is a Group Policy Object?
A Group Policy Object is a collection of configurations that are defined for a specific system or user. There are three types of Group Policy Objects—local, non-local, and starter.
1. Local
Refers to the collection of group policy settings that apply only to the local computer and to users who log on to a specific computer.
2. Non-local
Used when policy settings have to apply to one or more systems or users.
3. Starter
Enable an administrator to create a pre-configured group of settings that represent a baseline for any future policies.
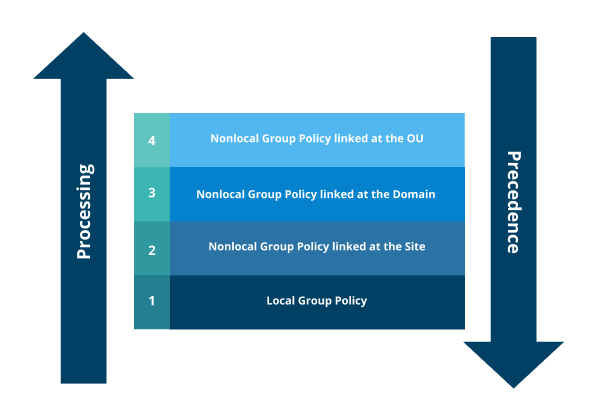
Most commonly, Group Policies are processed in the following order, with the Group Policy that is processed first having the least precedence and the one that is processed last having the most precedence.
Five Best Practices for Group Policy Objects
1. Add comments that explain why the policy was created
2. Create a well-designed organization unit structure in Active Directory
3. Delete the link from an organization unit rather than disabling Group Policy Objects
4. Do not:
- Set Group Policy Objects at the domain level
- Use the root computers
- Use folders in Active Directory
5. Do:
Use descriptive names
How Are Group Policy Objects Processed?
The processing order for Group Policies, also known as LSDOU (i.e., local, site, domain, organization unit), determines what settings are applied to users and computers. When multiple Group Policy Objects are linked to a single Active Directory container, they are processed in order of link, starting from the highest link order number to lowest to take effect.
The steps for processing Group Policy Objects are:
1. The local computer policy is processed.
2. Active Directory policies from site level to domain are processed.
3. Organizational units are processed. Note that for GPOs in nested organization units, the one closest to the root is processed first. If there are any conflicts, the last applied policy will take effect.
When Group Policy Objects are evaluated, several properties determine whether the setting they contain will be processed, including:
- Is the group policy link active or inactive?
- Is the object in the scope Access Control List (ACL) of the Group Policy Object (GPO)?
- Are either the computer or user sections of the policy disabled?
- Is Windows Management Instrumentation (WMI) filtering enabled on the GPO? If so, does the object match the filter?
Settings can be put in place to “Block Inheritance” for Group Policy Objects or “Enforce” a link setting. An “Enforced” link setting prevents the policy from being overridden by a policy that is processed later. It also means that the settings in this policy apply even if another object is set to “Block Inheritance.”
Who Should Use Group Policy?
Group Policy is a hierarchical infrastructure that helps network administrators implement specific configurations for users and computers, such as:
- Deploying software
- Applying security systems and updates
- Controlling users’ environments
- Standardizing desktop environments
- Modifying registries
Other ways to use Group Policy include:
- Configuring policy-based Quality of Service (QoS)
- Disabling forced restarts
- Disabling software installations
- Managing new wired network (IEEE 802.3) or wireless network (IEEE 802.11) policy settings
- Preventing use of removable media drives (e.g., USB sticks, external hard drives)
- Preventing users from launching Microsoft Store apps
- Restricting Command Prompt access to run scripts
- Securing end-to-end IPsec connections
- Setting control panel access (i.e., limiting or blocking it)
- Turning off OneDrive and/or Windows Defender
Benefits of Group Policy
- Configure folder redirection
- Deploy software and patches
- Enforce internet policies and password rules (e.g., password length, reuse)
- Expedite deployment of updated settings to all users
- Prevent user vulnerabilities, such as unauthorized access to specific resources and running scripts
- Provide uniform user experiences across multiple systems (e.g., desktop, laptop, mobile devices)
- Reduce IT expenses
- Standardize functionality, security, and management control
Group Policy Limitations
- Delayed user log on due to Group Policy Objects running sequentially
- Difficult to use (e.g., administrators will require knowledge of PowerShell to update Group Policy Objects)
- Inability to react to changes in the environment, such as a network disconnect or reconnect
- Increased complexity as Group Policy designs expand, including inheritance options and interaction between multiple policies
- Lack of built-in search or filter options to find a specific setting within a Group Policy Objects makes it difficult to find or fix issues with existing settings
- Large number of policy settings and preference items
- Limited flexibility to apply settings based on context, since Group Policy Objects can only be applied to users or computers
- Limited triggers, since Group Policy Objects can only be applied at computer startup
- No version control, which means that if an incorrect change is made, there is not an audit trail
- Updates to Group Policy Objects have a default to run an update every seven seconds, which can create unnecessary network traffic
- Vulnerability to cyberattacks if Group Policy Objects are accessed to travel laterally across the network
Group Policy—An Oldie, But a Goodie
Group Policy has been around for a long time and is still widely used. It is the go-to tool for managing and applying changes across Windows environments. And, it provides material benefits.
Correctly configured Group Policy Objects optimize productivity and security. Group Policy is an accessible tool that helps administrators effectively manage users, access, hardware, and solutions.
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 16,000 customers with millions of customers worldwide.
Last Updated: 10h March, 2022




