Trusted by 22,000+ Content-Critical Businesses Worldwide
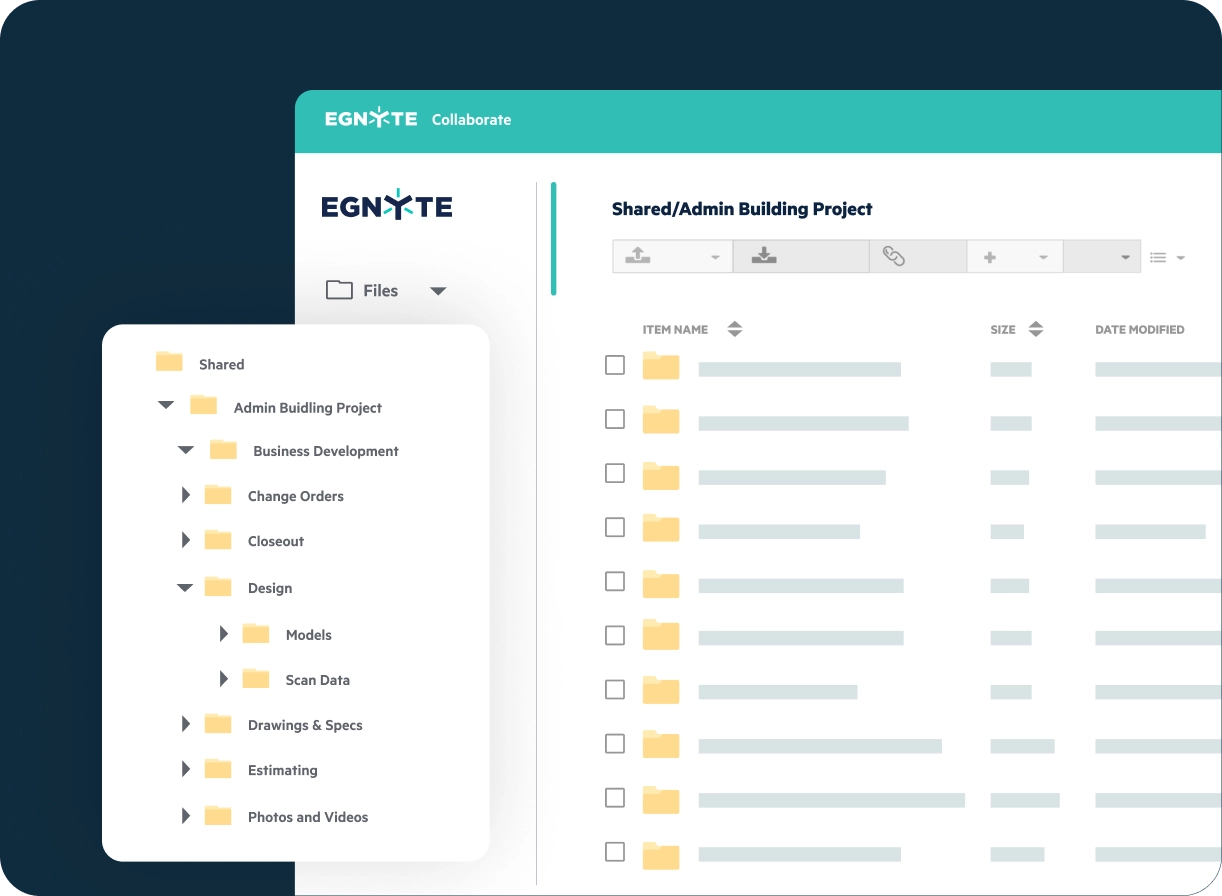
Unified Document Management and Control
Sensitive Data Discovery and Classification
Automate the discovery, classification and continuous monitoring of sensitive data across cloud and on-premises sources, with out-of-the-box classification patterns and a unified control dashboard.
Ransomware Risk Mitigation
Protect business content from ransomware attacks with signature and behavior-based detection, report on compromised users, files and data subjects, and automate data recovery with file snapshots.
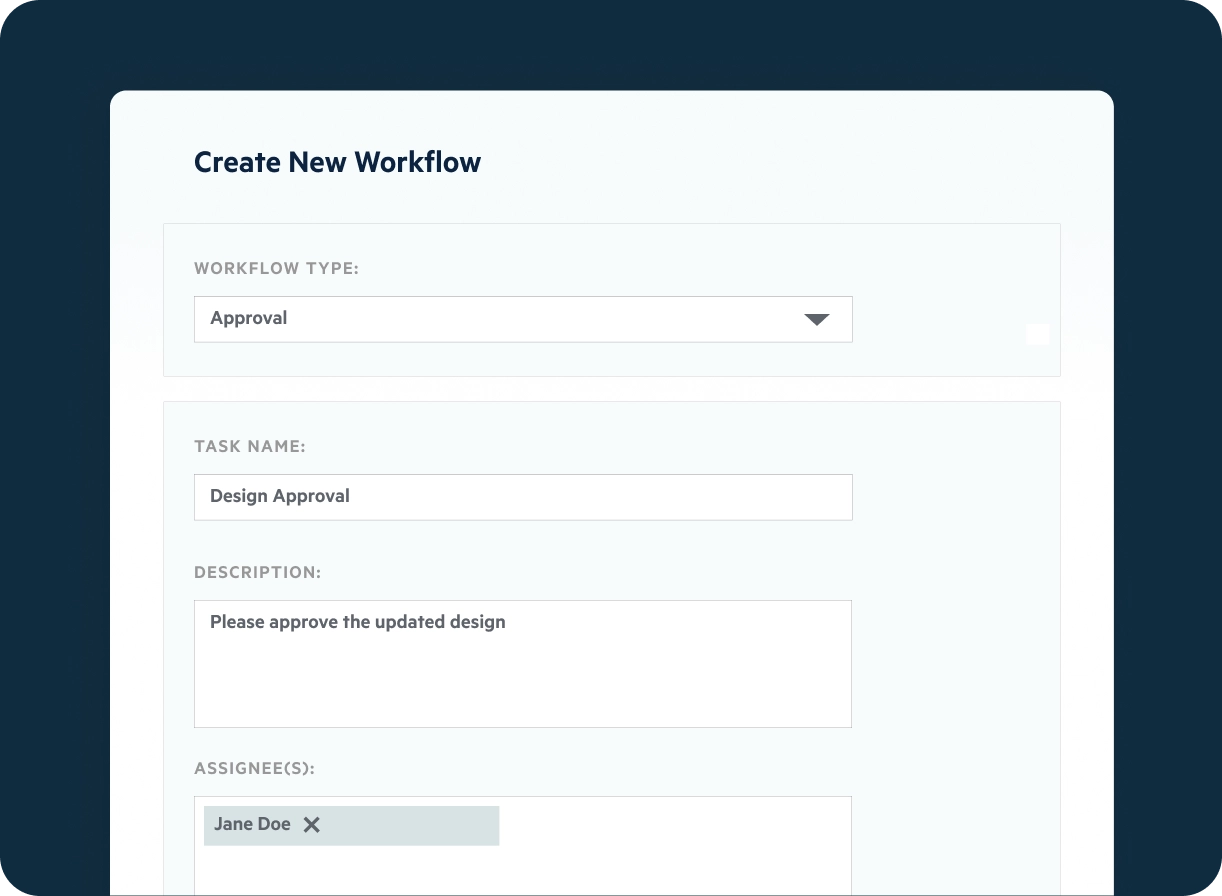
Multi-Cloud Data Management
Automate content lifecycle workflows for RAD/ROTS and SAR/DSAR fulfillment using built-in policies and a unified dashboard to manage, audit and generate compliance reporting.

Data Leakage Protection
Prevent unauthorized file access with sharing safeguards and granular permissions, while proactively detecting and alerting to suspicious logins and other anomalous user and file behavior.
Plans for Companies of All Sizes
Business
- File versioning
- Folder templates
- Desktop and mobile access
- Single-step workflows
Enterprise Lite
- Multi-step workflows
- Legal hold
- Mobile & desktop device controls
- Role-based access controls
Ultimate
- AI Copilot, AI Search, and AI Workflow
- PDF markup and e-signature
- Sensitive data classification
- Snapshot & recovery (90-days)
Popular Add-Ons for Data Security and Governance
Data Security and GovernanceDiscover, manage and protect sensitive content in 3rd-party cloud and on-premises sources.
Discover, manage and protect sensitive content in 3rd-party cloud and on-premises sources.
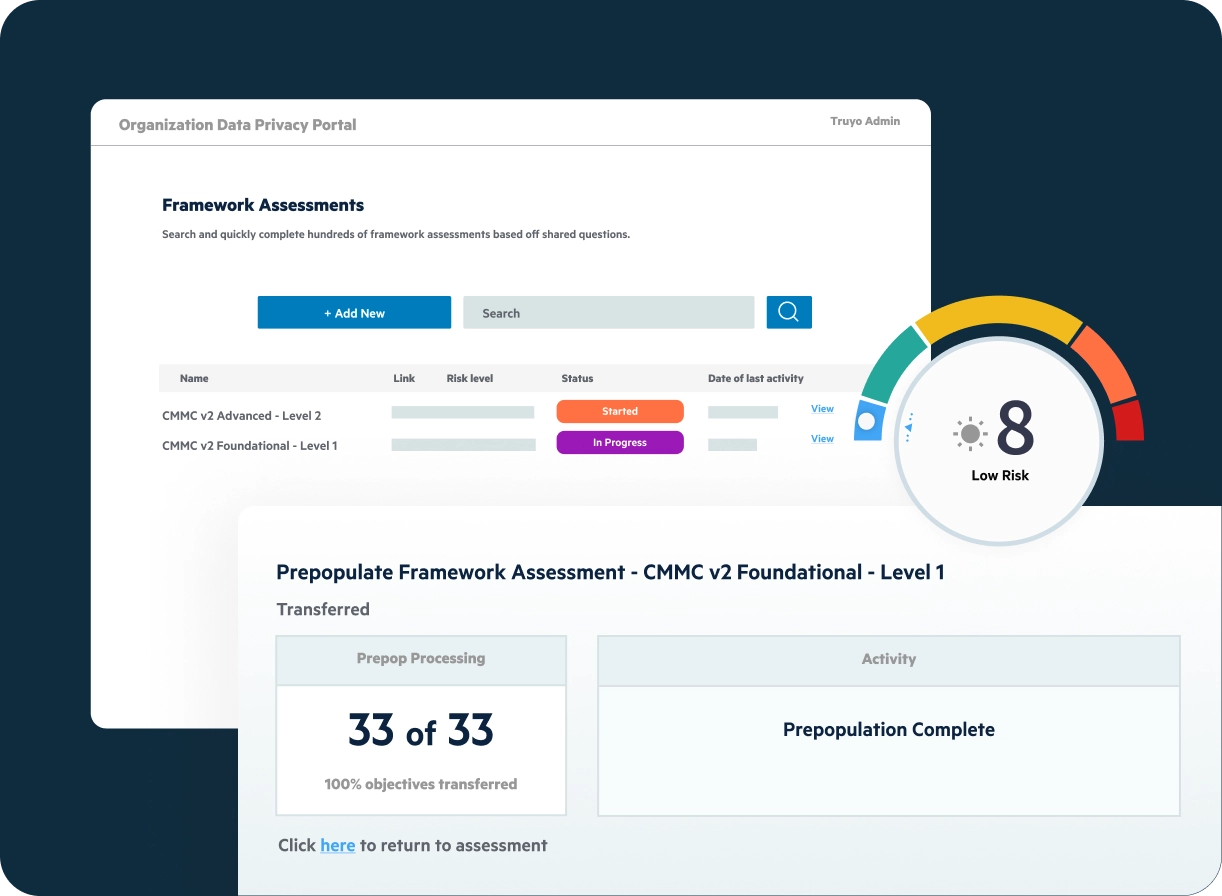
Infosec and Privacy Control FrameworksSimplify and streamline compliance documentation and workflow.
Simplify and streamline compliance documentation and workflow.
Document RoomProtect your most sensitive data in an ultra-secure enclave.
Protect your most sensitive data in an ultra-secure enclave.






